8 Passwords and Keys: Signing and Encrypting Data
The GNOME Passwords and Keys program is an important component of the encryption infrastructure on your system. With this program, you can create and manage PGP and SSH keys, import, export and share keys, back up your keys and keyring, and cache your passphrase.
To start the application open the Activities Overview by pressing Meta and search for pass.
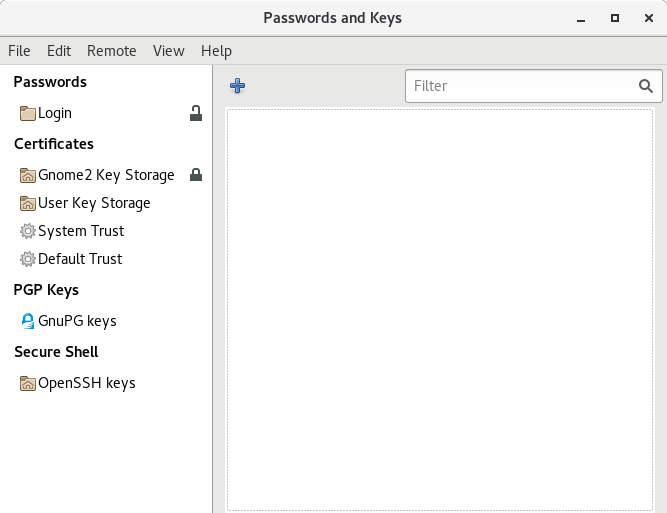
Figure 8.1: Password and Keys Main Window #
8.1 Signing and Encryption #
Signing. Attaching electronic signatures to pieces of information, such as e-mail messages or software to prove its origin. To keep someone else from writing messages using your name, and to protect both you and the people you send them to, you should sign your mails. Signatures help you check the sender of the messages you receive and distinguish authentic messages from malicious ones.
Software developers sign their software so that you can check the integrity. Even if you get the software from an unofficial server, you can verify the package with the signature.
Encryption. You might also have sensitive information you want to protect from other parties. Encryption helps you transform data and make it unreadable for others. This is important for companies so they can protect internal information and their employees' privacy.
8.2 Generating a New Key Pair #
To exchange encrypted messages with other users, you must first generate your own pair of keys. It consists of two parts:
Public Key. This key is used for encryption. Distribute it to your communication partners, so they can use it to encrypt files or messages for you.
Private Key. This key is used for decryption. Use it to make encrypted files or messages from others (or yourself) legible again.
Important: Access to the Private Key
If others gain access to your private key, they can decrypt files and messages intended only for you. Never grant others access to your private key.
8.2.1 Creating OpenPGP Keys #
OpenPGP is a non-proprietary protocol for encrypting e-mail with the use of public-key cryptography based on PGP. It defines standard formats for encrypted messages, signatures, private keys, and certificates for exchanging public keys.
Click › › .
Click › .
Select and click .
Specify your full name and e-mail address.
Click to specify the following advanced options for the key.
- Comment
An optional comment.
- Encryption Type
Specifies the encryption algorithms used to generate your keys. is the recommended choice because it lets you encrypt, decrypt, sign, and verify as needed. Both and allow only signing.
- Key Strength
Specifies the length of the key in bits. The longer the key, the more secure it is (provided a strong passphrase is used). Keep in mind that performing any operation with a longer key requires more time than it does with a shorter key. Acceptable values are between 1024 and 4096 bits. At least 2048 bits are recommended.
- Expiration Date
Specifies the date at which the key will cease to be usable for performing encryption or signing operations. You will need to either change the expiration date or generate a new key or subkey after this amount of time passes. Sign your new key with your old one before it expires to preserve your trust status.
Click to create the new key pair.
The dialog opens.
Specify the passphrase twice for your new key, then click .
When you specify a passphrase, use the same practices you use when you create a strong password.
8.2.2 Creating Secure Shell Keys #
Secure Shell (SSH) is a method of logging in to a remote computer to execute commands on that machine. SSH keys are used in key-based authentication system as an alternative to the default password authentication system. With key-based authentication, there is no need to manually type a password to authenticate.
Click › › .
Click › .
Select , then click .
Specify a description of what the key is to be used for.
You can use your e-mail address or any other reminder.
Optionally, click to specify the following advanced options for the key.
Encryption Type. Specifies the encryption algorithms used to generate your keys. Select to use the Rivest-Shamir-Adleman (RSA) algorithm to create the SSH key. This is the preferred and more secure choice. Select to use the Digital Signature Algorithm (DSA) to create the SSH key.
Key Strength. Specifies the length of the key in bits. The longer the key, the more secure it is (provided a strong passphrase is used). Keep in mind that performing any operation with a longer key requires more time than it does with a shorter key. Acceptable values are between 1024 and 4096 bits. At least 2048 bits is recommended.
Click to create the new key, or click to create the key and set up another computer to use for authentication.
Specify the passphrase for your new key, click , then repeat.
When you specify a passphrase, use the same practices you use when you create a strong password.
8.3 Modifying Key Properties #
You can modify properties of existing OpenPGP or SSH keys.
8.3.1 Editing OpenPGP Key Properties #
The descriptions in this section apply to all OpenPGP keys.
Click › › .
Double-click the PGP key you want to view or edit.
Use the options on the tab to add a photo to the key or to change the passphrase associated with the key.
Photo IDs allow a key owner to embed one or more pictures of themselves in a key. These identities can be signed like normal user IDs. A photo ID must be in JPEG format. The recommended size is 120×150 pixels.
If the chosen image does not meet the required file type or size, can resize and convert it on the fly from any image format supported by the GDK library.
Click the tab to add a user ID to a key.
See Section 8.3.1.1, “Adding a User ID” for more information.
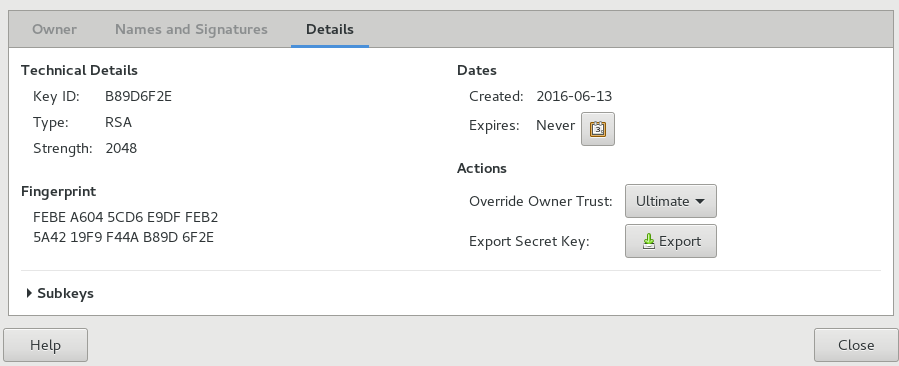
Click the tab, which contains the following properties:
Key ID: The Key ID is similar to the Fingerprint, but the Key ID contains only the last eight characters of the fingerprint. It is generally possible to identify a key with only the Key ID, but sometimes two keys might have the same Key ID.
Type: Specifies the encryption algorithm used to generate a key. DSA keys can only sign. ElGamal keys are used to encrypt.
Strength: Specifies the length, in bits, of the key. The longer the key, the more security it provides. However, a long key will not compensate for the use of a weak passphrase.
Fingerprint: A unique string of characters that exactly identifies a key.
Created: The date the key was created.
Expires: The date the key can no longer be used (a key can no longer be used to perform key operations after it has expired). Changing a key's expiration date to a point in the future re-enables it. A good general practice is to have a master key that never expires and multiple subkeys that do expire and are signed by the master key.
Override Owner Trust: Here you can set the level of trust in the owner of the key. Trust is an indication of how sure you are of a person's ability to correctly extend the Web of trust. When there is a key that you have not signed, the validity of the key is determined from its signatures and how much you trust the people who made those signatures.
Export Secret Key: Exports the key to a file.
Subkeys: See Section 8.3.1.2, “Editing OpenPGP Subkey Properties” for more information.
Click .
8.3.1.1 Adding a User ID #
User IDs allow multiple identities and e-mail addresses to be used with the same key. Adding a user ID is useful, for example, when you want to have an identity for your job and one for your friends. They take the following form:
Name (COMMENT) <E-MAIL>
Click › › .
Double-click the PGP key you want to view or edit.
Click the tab, then click .
Specify a name in the field.
You must enter at least five characters in this field.
Specify an e-mail address in the field.
Your e-mail address is how most people will locate your key on a key server or other key provider. Make sure it is correct before continuing.
In the field, specify additional information that will display in the name of your new ID.
This information can be searched for on key servers.
Confirm your changes and enter the passphrase when prompted for it.
8.3.1.2 Editing OpenPGP Subkey Properties #
Each OpenPGP key has a single master key used to sign only. Subkeys are used to encrypt and to sign as well. In this way, if your subkey is compromised, you do not need to revoke your master key.
Click › › .
Double-click the PGP key you want to edit.
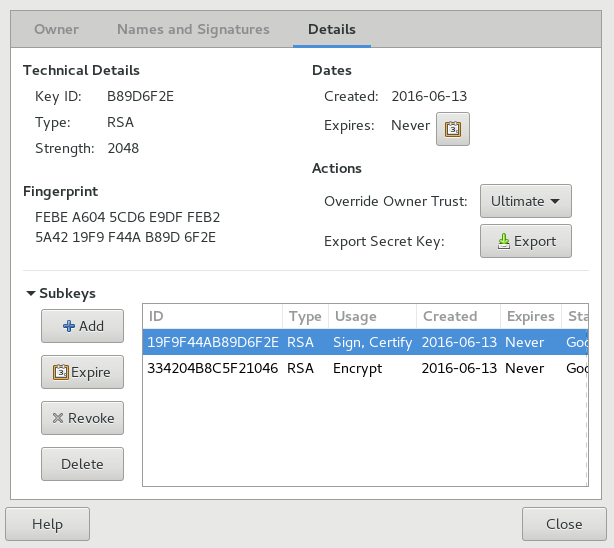
Click the tab, then click to show the category.
Use the buttons on the left of the dialog to add, delete, expire, or revoke subkeys.
Each subkey has the following information:
ID: The identifier of the subkey.
Type: Specifies the encryption algorithm used to generate a subkey. DSA keys can only sign, ElGamal keys are used to encrypt, and RSA keys are used to sign or to encrypt.
Usage: Shows if the key can be used to sign, to certify, or also to encrypt.
Created: Specifies the date the key was created.
Expires: Specifies the date the key can no longer be used.
Status: Specifies the status of the key.
Strength: Specifies the length, in bits, of the key. The longer the key, the more security it provides. However, a long key will not compensate for the use of a weak passphrase.
Click .
8.3.2 Editing Secure Shell Key Properties #
The descriptions in this section apply to all SSH keys.
Click › › .
Double-click the Secure Shell key you want to view or edit.
Use the options on the tab to change the name of the key or the passphrase associated with the key.
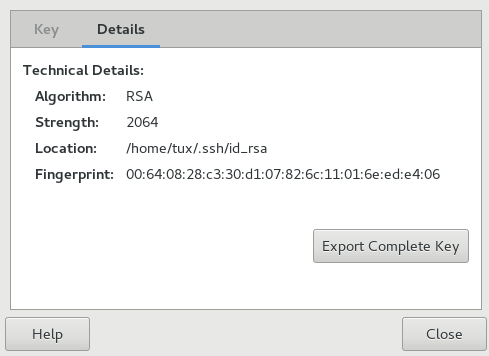
Click the tab, which contains the following properties:
Algorithm: Specifies the encryption algorithm used to generate a key.
Strength: Indicates the length in bits of a key. The longer the key, the more security it provides. However, a long key does not make up for the use of a weak passphrase.
Location: The location where the private key has been stored.
Fingerprint: A unique string of characters that exactly identifies a key.
Export Complete Key: Exports the key to a file.
Click .
8.4 Importing Keys #
Keys can be exported to text files. These files contain human-readable text at the beginning and at the end of a key. This format is called an ASCII-armored key.
To import keys:
Click › › .
Click › .
Select a file containing at least one ASCII-armored public key.
Click to import the key.
You can also paste keys inside :
Select an ASCII-armored public block of text, then copy it to the clipboard.
Click › › .
Click ›
8.5 Exporting Keys #
To export keys:
Click › › .
Select the keys you want to export.
Click › .
Specify a file name and location for the exported key.
Click to export the key.
You can also export keys to the clipboard in an ASCII-armored block of text:
Click › › .
Select the keys you want to export.
Click › .
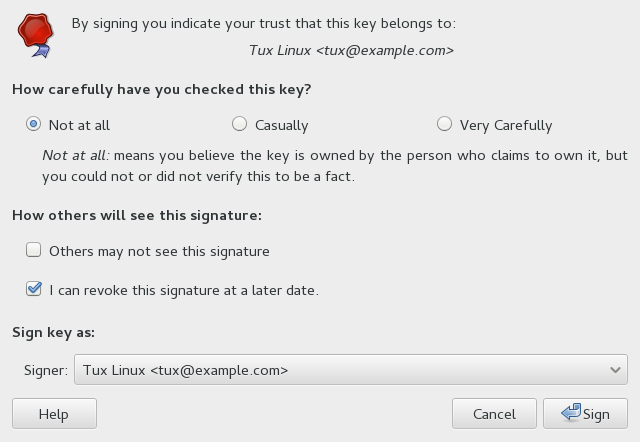
8.6 Signing a Key #
Signing another person's key means that you are giving trust to that person. Before signing a key, carefully check the key's fingerprint to ensure that the key really belongs to that person.
Trust is an indication of how sure you are of a person's ability to correctly extend the Web of trust. When there is a key that you have not signed, the validity of the key is determined from its signatures and how much you trust the people who made those signatures.
8.7 File Manager Integration #
Passwords and Keys integrates with GNOME Files. You can encrypt, decrypt, sign, verify files, and import public keys from the file manager window without launching .
Note: Enabling File Manager Integration
The package nautilus-extension-seahorse has to be
installed to enable file manager integration.
8.7.1 Encrypting Files From GNOME Files #
In GNOME Files, right-click the files you want to encrypt.
Select .
Select the people (recipients) you want to encrypt the file to, then click .
If prompted, specify the passphrase of your private key, then click .
8.7.2 Signing Files From GNOME Files #
In GNOME Files, right-click the files you want to sign.
Select .
Select a signer, then click .
If prompted, specify the passphrase of your private key, then click .
8.7.3 Decrypting Files From GNOME Files #
To decrypt an encrypted file in GNOME Files, simply double-click the file you want to decrypt.
If prompted, specify the passphrase of your private key.
8.7.4 Verifying Signatures From GNOME Files #
To verify files, simply double-click the detached signature file. Detached
signature file names often have a .sig extension.
8.8 Password Keyrings #
You can use password keyring preferences to create or remove keyrings, to set the default keyring for application passwords or to change the unlock password of a keyring. To create a new keyring, follow these steps:
Click › › .
Click › › , then click .
Enter a name for the keyring and click .
Set and confirm a new for the keyring and click .
To change the unlock password of an existing keyring, right-click the keyring in the tab and click . You need to provide the old password to be able to change it.
To change the default keyring for application passwords, right-click the keyring in the tab and click .
8.9 Key Servers #
You can keep your keys up-to-date by synchronizing keys periodically with remote key servers. Synchronizing will ensure that you have the latest signatures made on all of your keys, so that the Web of trust will be effective.
Click › › .
Click › , then click the tab.
provides support for HKP and LDAP key servers.
HKP Key Servers: HKP key servers are ordinary Web-based key servers, such as the popular
hkp://pgp.mit.edu:11371, also accessible at http://pgp.mit.edu.LDAP Key Servers: LDAP key servers are less common, but use the standard LDAP protocol to serve keys.
ldap://keyserver.pgp.comis a good LDAP server.You can or key servers to be used using the buttons on the left. To add a new key server, set its type, host and port, if necessary.
Set whether you want to automatically publish your public keys and which key server to use. Set whether you want to automatically retrieve keys from key servers and whether to synchronize modified keys with key servers.
Click .
8.10 Key Sharing #
Key Sharing is provided by DNS-SD, also known as Bonjour or Rendezvous. Enabling key sharing adds the local users' public key rings to the remote search dialog. Using these local key servers is generally faster than accessing remote servers.
Click › › .
Click › , then click the tab.
Select .
Click .