3 Installation Steps Edit source
Abstract#
This chapter describes the procedure in which the data for openSUSE Leap is copied to the target device. Some basic configuration parameters for the newly installed system are set during the procedure. A graphical user interface will guide you through the installation. The text mode installation has the same steps and only looks different. For information about performing non-interactive automated installations, see Book “AutoYaST Guide”.
- 3.1 Overview
- 3.2 Installer Self-Update
- 3.3 Language, Keyboard, and License Agreement
- 3.4 Network Settings
- 3.5 Online Repositories
- 3.6 System Role
- 3.7 Partitioning
- 3.8 Clock and Time Zone
- 3.9 Create New User
- 3.10 Authentication for the System Administrator “root”
- 3.11 Installation Settings
- 3.12 Performing the Installation
If you are a first-time user of openSUSE Leap, you should follow the default YaST proposals in most parts, but you can also adjust the settings as described here to fine-tune your system according to your preferences. Help for each installation step is provided by clicking .
Tip: Installation Without a Mouse
If the installer does not detect your mouse correctly, use →| for navigation, arrow keys to scroll, and Enter to confirm a selection. Various buttons or selection fields contain a letter with an underscore. Use Alt–Letter to select a button or a selection directly instead of navigating there with →|.
3.1 Overview #Edit source
This section provides an overview of all installation steps. Each step contains a link to a more detailed description.
Before the installation starts, the installer can update itself. For details, see Section 3.2, “Installer Self-Update”.
The actual installation starts with choosing the language and accepting the license agreement. For details, see Section 3.3, “ Language, Keyboard, and License Agreement ”.
Configure the network. This is only required when you need network access during the installation and the automatic network configuration via DHCP failed. If the automatic network configuration succeeded, this step is skipped. For details, see Section 3.4, “Network Settings”.
Configure the online repositories. By adding official openSUSE repositories, you get access to more software and get the latest security updates already during installation. For details, see Section 3.5, “Online Repositories”. This step is optional and can be skipped.
Select a desktop or a role for your system. Among other things, this defines the default list of packages to install and makes a suggestion for partitioning the hard disks. For details, see Section 3.6, “System Role”.
Partition the hard disks of your system. For details, see Section 3.7, “Partitioning”.
Choose a time zone. For details, see Section 3.8, “Clock and Time Zone”.
Create a user. For details, see Section 3.9, “Create New User”.
Optionally, set a different password for the system administrator
root. For details, see Section 3.10, “Authentication for the System Administrator “root””.In a final step, the installer presents an overview of all settings. If required, you can change them. For details, see Section 3.11, “Installation Settings”.
The installer copies all required data and informs you about the progress. For details, see Section 3.12, “Performing the Installation”.
3.2 Installer Self-Update #Edit source
During the installation and upgrade process, YaST can update itself to
solve bugs in the installer that were discovered after the release. This
functionality is enabled by default; to disable it, set the boot parameter
self_update to 0. For more information,
see Section 2.4.4, “Enabling the Installer Self-Update”.
Important: Quarterly Media Update: Self-Update Disabled
The installer self-update is only available if you use the GM
images of the Unified Installer and Packages ISOs. If you install from the ISOs published
as quarterly update (they can be identified by the string QU
in the name), the installer cannot update itself, because this feature has
been disabled in the updated media.
Important: Networking during Self-Update
To download installer updates, YaST needs network access. By default, it tries to use DHCP on all network interfaces. If there is a DHCP server in the network, it will work automatically.
If you need a static IP setup, you can use the ifcfg
boot argument. For more details, see the linuxrc documentation at
https://en.opensuse.org/Linuxrc.
Tip: Language Selection
The installer self-update is executed before the language selection step. This means that progress and errors which happen during this process are displayed in English by default.
To use another language for this part of the installer, use the
language boot parameter if available for your
architecture, for example, language=de_DE. On machines
equipped with a traditional BIOS, alternatively, press F2
in the boot menu and select the language from the list.
Although this feature was designed to run without user intervention, it is worth knowing how it works. If you are not interested, you can jump directly to Section 3.3, “ Language, Keyboard, and License Agreement ” and skip the rest of this section.
3.2.1 Self-Update Process #Edit source
The process can be broken down into two different parts:
Determine the update repository location.
Download and apply the updates to the installation system.
3.2.1.1 Determining the Update Repository Location #Edit source
Installer Self-Updates are distributed as regular RPM packages via a dedicated repository, so the first step is to find out the repository URL.
Important: Installer Self-Update Repository Only
No matter which of the following options you use, only the installer self-update repository URL is expected, for example:
self_update=https://www.example.com/my_installer_updates/
Do not supply any other repository URL—for example the URL of the software update repository.
YaST will try the following sources of information:
The
self_updateboot parameter. (For more details, see Section 2.4.4, “Enabling the Installer Self-Update”.) If you specify a URL, it will take precedence over any other method.The
/general/self_update_urlprofile element in case you are using AutoYaST.If none of the previous attempts worked, the fallback URL (defined in the installation media) will be used.
3.2.1.2 Downloading and Applying the Updates #Edit source
When the updates repository is determined, YaST will check whether an update is available. If so, all the updates will be downloaded and applied to the installation system.
Finally, YaST will be restarted to load the new version and the welcome screen will be shown. If no updates were available, the installation will continue without restarting YaST.
Note: Update Integrity
Update signatures will be checked to ensure integrity and authorship. If a signature is missing or invalid, you will be asked whether you want to apply the update.
3.2.1.3 Temporary Self-Update Add-on Repository #Edit source
Some packages distributed in the self-update repository provide additional data for the installer, like the installation defaults, system role definitions and similar. If the installer finds such packages in the self-update repository, a local temporary repository is created, to which those packages are copied. They are used during the installation process, but at the end of the installation, the temporary local repository is removed. Its packages are not installed onto the target system.
This additional repository is not displayed in the list of add-on
products, but during installation it may still be visible as
SelfUpdate0 repository in the package management.
3.2.2 Custom Self-Update Repositories #Edit source
YaST can use a user-defined repository instead of the official one by
specifying a URL through the self_update boot parameter.
However, the following points should be considered:
Only HTTP/HTTPS and FTP repositories are supported.
Only RPM-MD repositories are supported (required by RMT).
Packages are not installed in the usual way: They are uncompressed only and no scripts are executed.
No dependency checks are performed. Packages are installed in alphabetical order.
Files from the packages override the files from the original installation media. This means that the update packages might not need to contain all files, only files that have changed. Unchanged files are omitted to save memory and download bandwidth.
Note: Only One Repository
Currently, it is not possible to use more than one repository as source for installer self-updates.
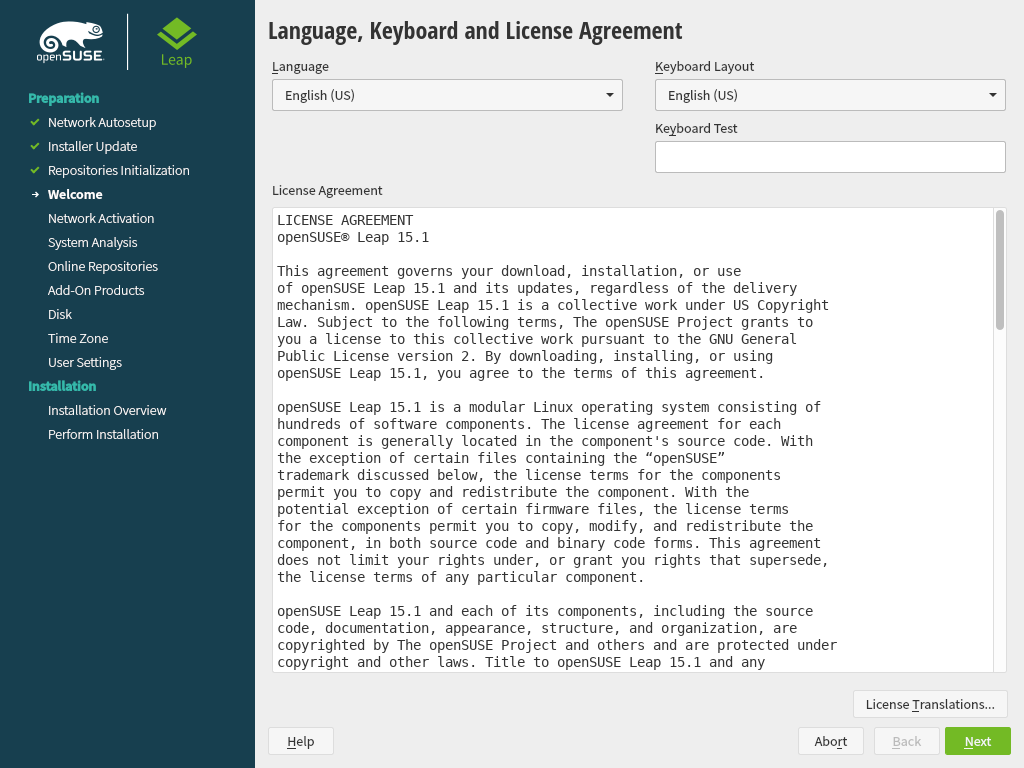
3.3 Language, Keyboard, and License Agreement #Edit source
Figure 3.1: Language, Keyboard, and License Agreement #
The and settings are initialized with the language you chose on the boot screen. If you did not change the default, it will be English (US). Change the settings here, if necessary.
Changing the language will automatically preselect a corresponding keyboard layout. Override this proposal by selecting a different keyboard layout from the drop-down box. Use the text box to test the layout. The language selected here is also used to assume a time zone for the system clock. This setting can be modified later in the installed system as described in Chapter 6, Changing Language and Country Settings with YaST.
Read the license agreement. It is presented in the language you have. Translations are available via the drop-down box. Proceed with if you agree to the terms and conditions. If you do not agree, click to terminate the installation.
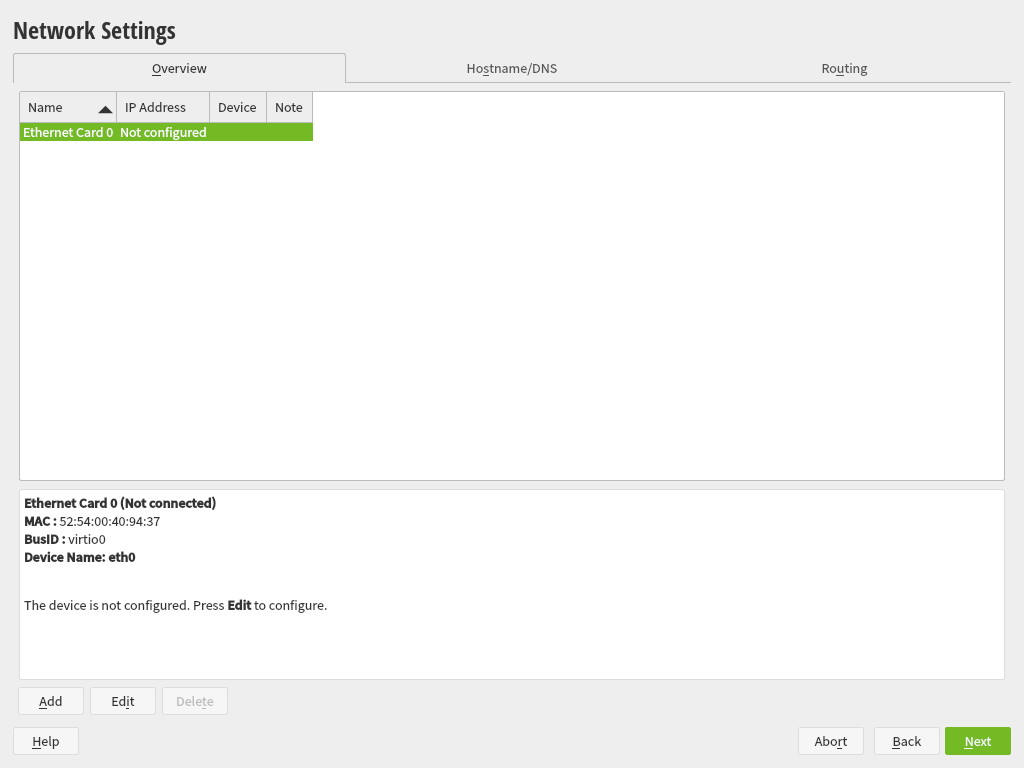
3.4 Network Settings #Edit source
After booting into the installation, the installation routine is set up. During this setup, an attempt to configure at least one network interface with DHCP is made. In case this attempt has failed, the dialog launches now.
Figure 3.2: Network Settings #
Choose a network interface from the list and click to change its settings. Use the tabs to configure DNS and routing. See Book “Reference”, Chapter 13 “Basic Networking”, Section 13.4 “Configuring a Network Connection with YaST” for more details.
In case DHCP was successfully configured during installation setup, you can also access this dialog by clicking at the the step. It lets you change the automatically provided settings.
Note: Network Configuration with Boot Parameters
If at least one network interface has been configured via boot parameters (see Section 2.3.2, “Configuring the Network Interface”), automatic DHCP configuration is disabled and the boot parameter configuration is imported and used.
Tip: Accessing Network Storage or Local RAID
To access a SAN or a local RAID during the installation, you can use the libstorage command line client for this purpose:
Switch to a console with Ctrl–Alt–F2.
Install the libstoragemgmt extension by running
extend libstoragemgmt.Now you have access to the
lsmclicommand. For more information, runlsmcli --help.To return to the installer, press Alt–F7
Supported are Netapp Ontap, all SMI-S compatible SAN providers, and LSI MegaRAID.
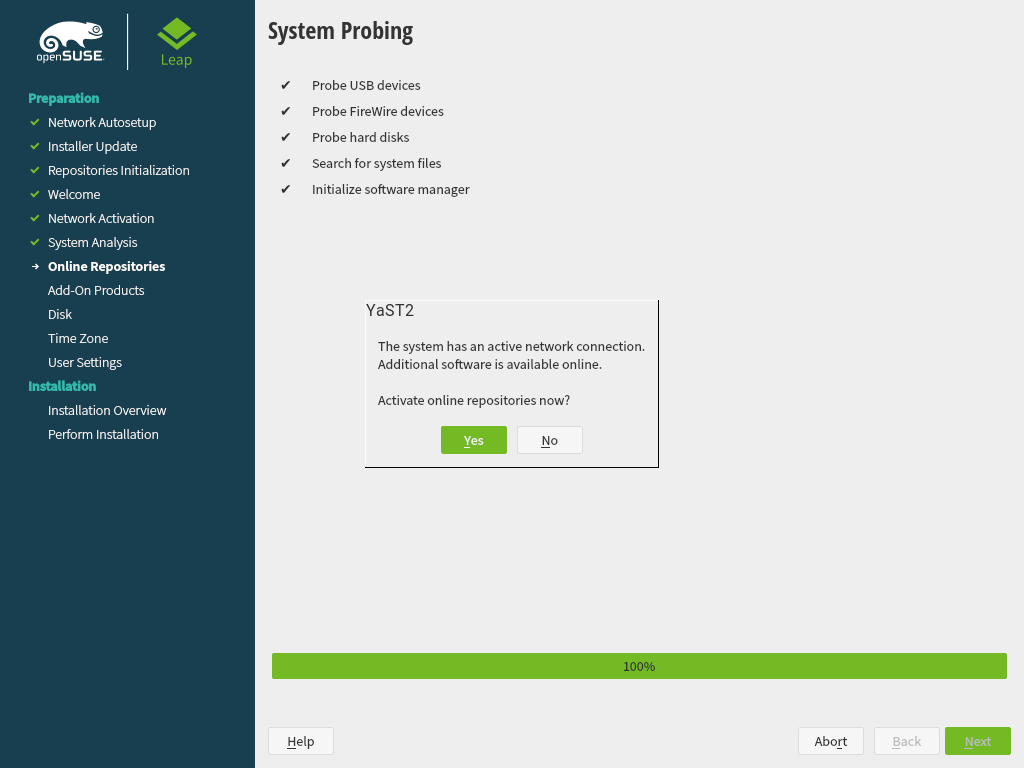
3.5 Online Repositories #Edit source
A system analysis is performed, where the installer probes for storage devices, and tries to find other installed systems. If a network connection with Internet access is available, you will be asked to activate the online repositories. Answer with to proceed. In case you do not have Internet access, this step will be skipped.
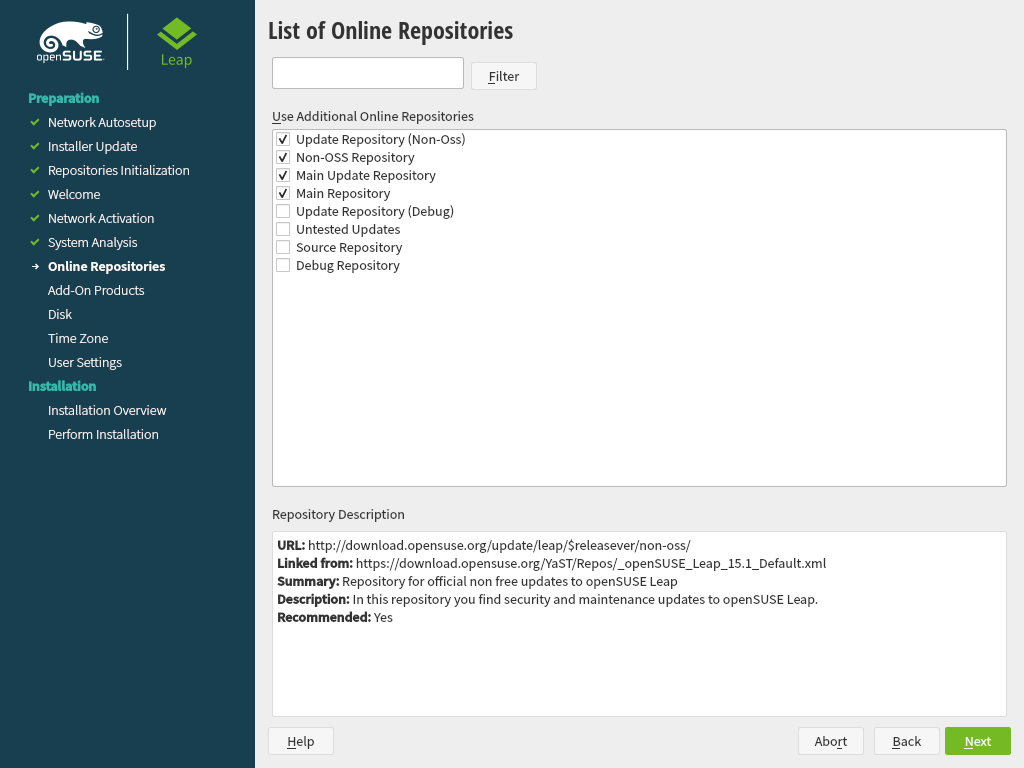
The online repositories are official openSUSE package sources. They not only offer additional packages not included on the installation media, but also the update repositories containing security and bug fixes. Using the default selection is recommended. Add at least the , because it makes sure the system is installed with the latest security patches.
You have the following choices:
The contains open source software (OSS). Compared to the DVD installation media, it contains many additional software packages, among them many additional desktop systems.
The contains security updates and fixes for packages from the and the DVD installation media. Choosing this repository is recommended for all installation scenarios.
The contains packages with a proprietary software license. Choosing it is not required for installing a custom desktop system.
Choosing is recommended when also having chosen the . It contains the respective updates and security fixes.
All other repositories are intended for experienced users and developers. Click on a repository name to get more information.
Confirm your selection with . Depending on your choice, you need to confirm one or more license agreements. Do so by choosing until you proceed to the screen. Now choose to proceed.
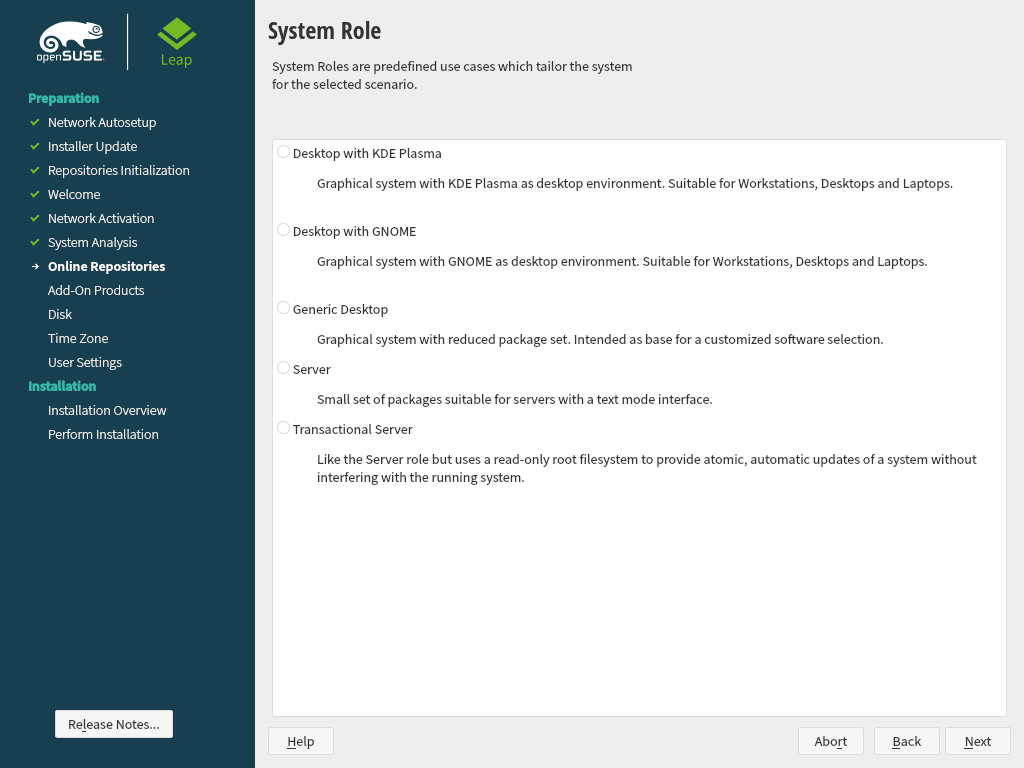
3.6 System Role #Edit source
openSUSE Leap supports a broad range of features. To simplify the installation, the installer offers predefined use cases which adjust the system to be installed so it is tailored for the selected scenario.
Figure 3.3: System Role #
Choose the that meets your requirements best. The availability of system roles depends on your selection of modules and extensions. Therefore, the dialog is omitted under the following conditions:
If from the enabled modules no role is suitable for the respective base product. In this case, the installation proceeds with the default settings for this product.
If from the enabled modules only one role is suitable for the respective base product. In this case, the installation proceeds with the settings of this particular role.
With the default selection, the following system roles are available:
A powerful desktop environment with a complete PIM suite (mail, calendar, tasks, notes, and feeds), widgets running on the desktop and many more features. If you are familiar with Windows, KDE is the recommended choice. For more information see https://kde.org/.
A desktop environment offering an alternative, innovative user experience. GNOME was designed with usability and productivity in mind. For more information see https://www.gnome.org/.
In case you prefer an alternative to the KDE or GNOME desktops, choose this option. You will be able to choose between the following alternatives later in the installation process by selecting in the :
Enlightenment (https://www.enlightenment.org/) LXDE (https://lxde.org/) LXQT (https://lxqt.org/) MATE (https://mate-desktop.org/) XFCE (https://xfce.org/) Note that when installing from the DVD all these desktop systems except XFCE are only available when having enabled the MAIN Repository (OSS) in the step. You can still enable this repository now by using the button until you reach the welcome screen. From there, choose and then agree to add online repositories.
If setting up a server, you probably do not need a graphical user interface and desktop applications such as an office suite. This option gives you a reduced set of packages suitable for servers.
Similar to the server role, but with a read-only root partition and transactional updates. This selection also is a prerequisite for setting up openSUSE Kubic. See https://kubic.opensuse.org/blog/2018-04-04-transactionalupdates/ for more information on transactional updates.
3.7 Partitioning #Edit source
3.7.1 Important Information #Edit source
Warning: Read this Section Carefully
Read this section carefully before continuing with Section 3.7.2, “Suggested Partitioning”.
- Custom Partitioning on UEFI Machines
A UEFI machine requires an EFI system partition that must be mounted to
/boot/efi. This partition must be formatted with theFAT32file system.If an EFI system partition is already present on your system (for example from a previous Windows installation) use it by mounting it to
/boot/efiwithout formatting it.If no EFI system partition is present on your UEFI machine, make sure to create it. The EFI system partition must be a physical partition or RAID 1. Other RAID levels, LVM and other technologies are not supported. It needs to be formatted with the FAT32 file system.
- Custom Partitioning and Snapper
If the root partition is larger than 16 GB, openSUSE Leap by default enables file system snapshots.
openSUSE Leap uses Snapper together with Btrfs for this feature. Btrfs needs to be set up with snapshots enabled for the root partition.
If the disk is smaller than 16 GB, all Snapper features and automatic snapshots are disabled to prevent the system partition
/from running out of space.Being able to create system snapshots that enable rollbacks requires important system directories to be mounted on a single partition, for example
/usrand/var. Only directories that are excluded from snapshots may reside on separate partitions, for example/usr/local,/var/log, and/tmp.For details, see Book “Reference”, Chapter 3 “System Recovery and Snapshot Management with Snapper”.

Important: Btrfs Snapshots and Root Partition Size
Snapshots occupy space on their partition. As a rule of thumb, the older a snapshot is, or the bigger the changeset they cover is, the bigger the snapshot. Plus, the more snapshots you keep, the more diskspace you need.
To prevent the root partition running full with snapshot data, you need to make sure it is big enough. In case you do frequent updates or other installations, consider at least 30 GB for the root partition. If you plan to keep snapshots activated for a system upgrade (to be able to roll back), you should consider 40 GB or more.
- Btrfs Data Volumes
Using Btrfs for data volumes is supported on openSUSE Leap 15.1. For applications that require Btrfs as a data volume, consider creating a separate file system with quota groups disabled. This is already the default for non-root file systems.
- Btrfs on an Encrypted Root Partition
The default partitioning setup suggests the root partition as Btrfs. To encrypt the root partition, make sure to use the GPT partition table type instead of the MSDOS type. Otherwise the GRUB2 boot loader may not have enough space for the second stage loader.
- Supported Software RAID Volumes
Installing to and booting from existing software RAID volumes is supported for Disk Data Format (DDF) volumes and Intel Matrix Storage Manager (IMSM) volumes. IMSM is also known by the following names:
Intel Rapid Storage Technology
Intel Matrix Storage Technology
Intel Application Accelerator / Intel Application Accelerator RAID Edition
Intel Virtual RAID on CPU (Intel VROC, see https://www.intel.com/content/www/us/en/support/articles/000024498/memory-and-storage/ssd-software.html for more details)
- Mount Points for FCoE and iSCSI Devices
FCoE and iSCSI devices will appear asynchronously during the boot process. While the initrd guarantees that those devices are set up correctly for the root file system, there are no such guarantees for any other file systems or mount points like
/usr. Hence any system mount points like/usror/varare not supported. To use those devices, ensure correct synchronization of the respective services and devices.- Handling of Windows Partitions in Proposals
In case the disk selected for the suggested partitioning proposal contains a large Windows FAT or NTFS partition, it will automatically be resized to make room for the openSUSE Leap installation. To avoid data loss it is strongly recommended to
make sure the partition is not fragmented (run a defragmentation program from Windows prior to the openSUSE Leap installation)
double-check the suggested size for the Windows partition is big enough
back up your data prior to the openSUSE Leap installation
To adjust the proposed size of the Windows partition, use the .
- Proposal with a Separate Home Partition
The default proposal no longer suggests to create a separate partition for
/home. The/homedirectory contains the user's data and personal configuration files. Placing it on a separate directory makes it easier to rebuild the system in the future, or allows to share it with different Linux installations on the same machine.In case you want to change the proposal to create a separate partition for
/home, choose and click until you reach the screen. Check . By default it will be formatted with , but you can choose to use a different file system. Close the dialog by clicking again.
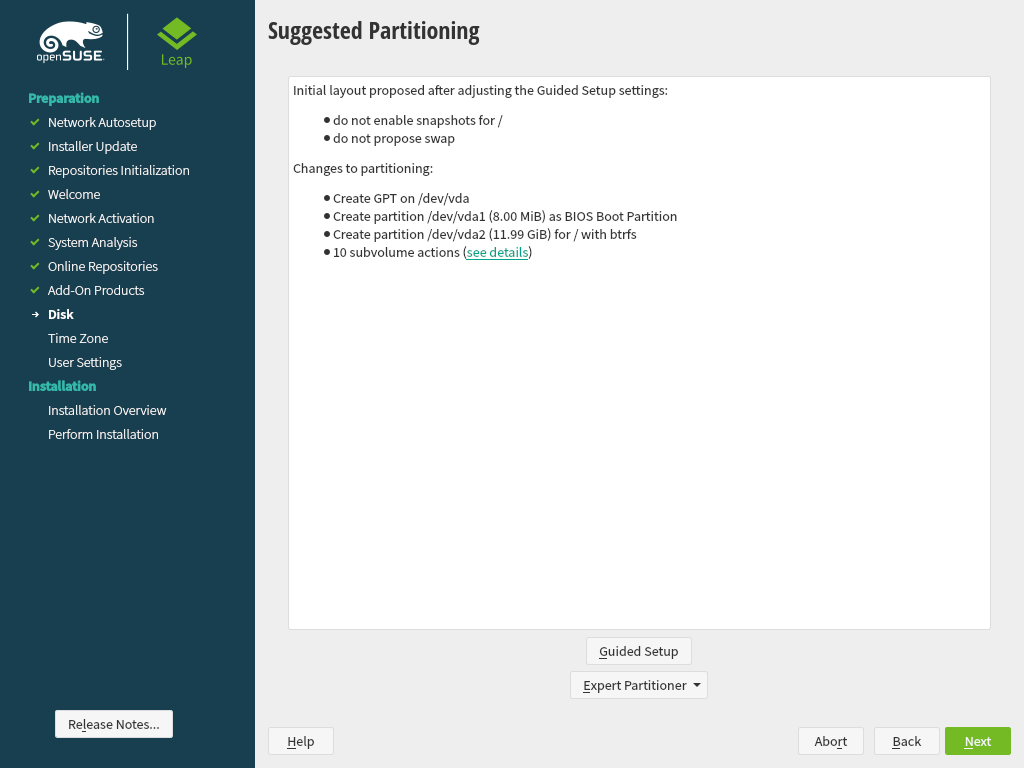
3.7.2 Suggested Partitioning #Edit source
Define a partition setup for openSUSE Leap in this step.
Figure 3.4: Suggested Partitioning #
The installer creates a proposal for one of the available disks containing a root partition formatted with Btrfs and a swap partition. If one or more swap partitions have been detected on the available hard disks, these partitions will be used. You have several options to proceed:
To accept the proposal without any changes, click to proceed with the installation workflow.
To adjust the proposal, choose . First, choose which hard disks and partitions to use. In the screen, you can enable Logical Volume Management (LVM) and activate disk encryption. Afterwards specify the . You can adjust the file system for the root partition and create a separate home and swap partitions. If you plan to suspend your machine, make sure to create a separate swap partition and check . If the root file system format is Btrfs, you can also enable or disable Btrfs snapshots here.
To create a custom partition setup click . Select either if you want start with the suggested disk layout, or to ignore the suggested layout and start with the existing layout on the disk. You can , , , or partitions.
You can also set up Logical Volumes (LVM), configure software RAID and device mapping (DM), encrypt Partitions, mount NFS shares and manage tmpfs volumes with the Expert Partitioner. To fine-tune settings such as the subvolume and snapshot handling for each Btrfs partition, choose . For more information about custom partitioning and configuring advanced features, refer to Book “Reference”, Chapter 5 “Expert Partitioner”, Section 5.1 “Using the Expert Partitioner”.
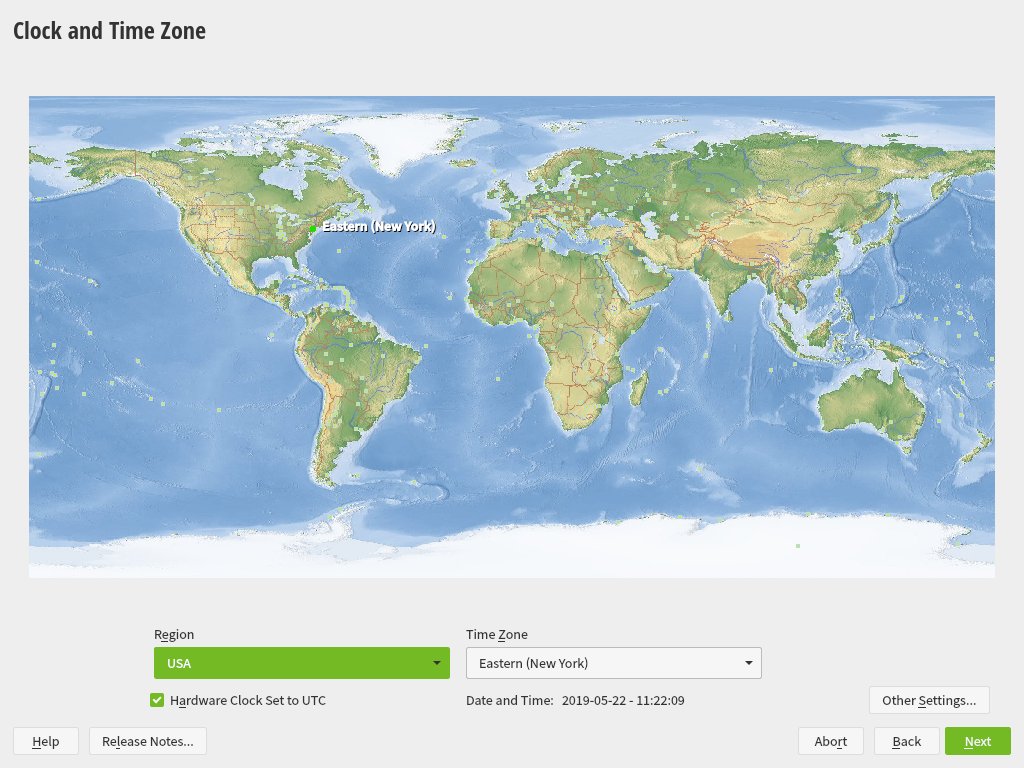
3.8 Clock and Time Zone #Edit source
In this dialog, select your region and time zone. Both are preselected according to the installation language.
Figure 3.5: Clock and Time Zone #
To change the preselected values, either use the map or the drop-down boxes for and . When using the map, point the cursor at the rough direction of your region and left-click to zoom. Now choose your country or region by left-clicking. Right-click to return to the world map.
To set up the clock, choose whether the . If you run another operating system on your machine, such as Microsoft Windows, it is likely your system uses local time instead. If you run Linux on your machine, set the hardware clock to UTC and have the switch from standard time to daylight saving time performed automatically.
Important: Set the Hardware Clock to UTC
The switch from standard time to daylight saving time (and vice versa) can only be performed automatically when the hardware clock (CMOS clock) is set to UTC. This also applies if you use automatic time synchronization with NTP, because automatic synchronization will only be performed if the time difference between the hardware and system clock is less than 15 minutes.
Since a wrong system time can cause serious problems (missed backups, dropped mail messages, mount failures on remote file systems, etc.), it is strongly recommended to always set the hardware clock to UTC.
If a network is already configured, you can configure time synchronization with an NTP server. Click to either alter the NTP settings or to set the time. See Book “Reference”, Chapter 18 “Time Synchronization with NTP” for more information on configuring the NTP service. When finished, click to continue the installation.
If running without NTP configured, consider setting
SYSTOHC=no (sysconfig variable) to
avoid saving unsynchronized time into the hardware clock.
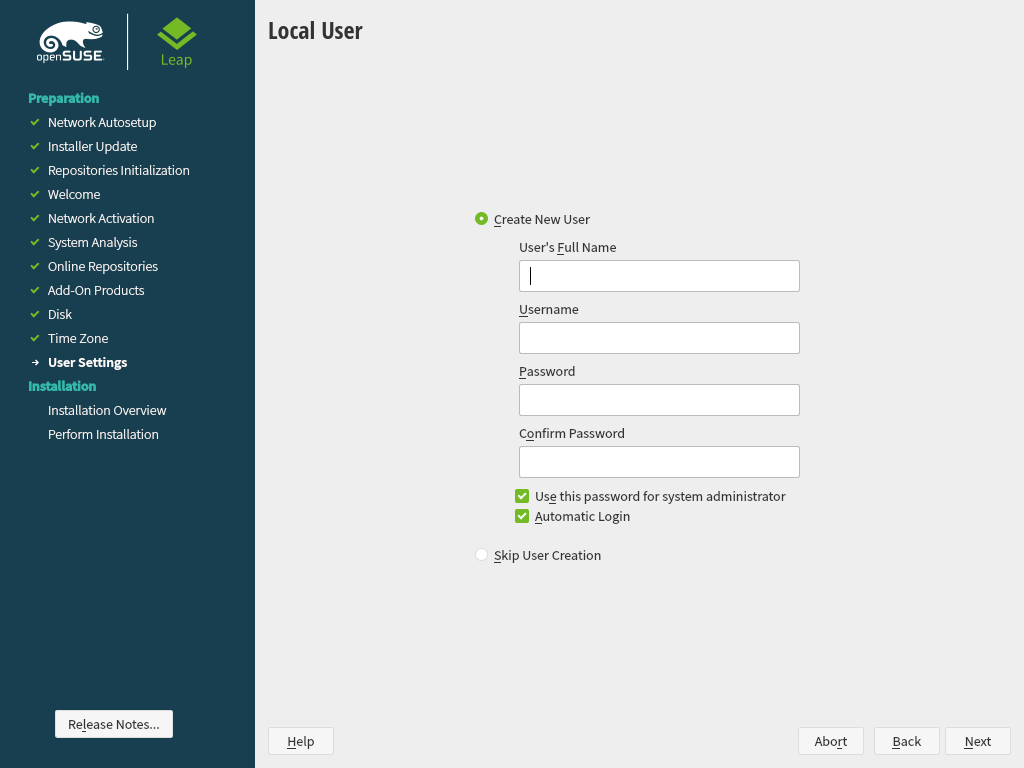
3.9 Create New User #Edit source
Create a local user in this step.
Figure 3.6: Create New User #
After entering the first name and last name, either accept the proposal or
specify a new that will be used to log in. Only
use lowercase letters (a-z), digits (0-9) and the characters
. (dot), - (hyphen) and
_ (underscore). Special characters, umlauts and accented
characters are not allowed.
Finally, enter a password for the user. Re-enter it for confirmation (to ensure that you did not type something else by mistake). To provide effective security, a password should be at least six characters long and consist of uppercase and lowercase letters, numbers and special characters (7-bit ASCII). Umlauts or accented characters are not allowed. Passwords you enter are checked for weakness. When entering a password that is easy to guess (such as a dictionary word or a name) you will see a warning. It is a good security practice to use strong passwords.
Important: User Name and Password
Remember both your user name and the password because they are needed each time you log in to the system.
If you install openSUSE Leap on a machine with one or more existing Linux installations, YaST allows you to import user data such as user names and passwords. Select and then for import.
If you do not want to configure any local users (for example when setting up a client on a network with centralized user authentication), skip this step by choosing and confirming the warning. Network user authentication can be configured at any time later in the installed system; refer to Chapter 5, Managing Users with YaST for instructions.
Two additional options are available:
If checked, the same password you have entered for the user will be used for the system administrator
root. This option is suitable for stand-alone workstations or machines in a home network that are administrated by a single user. When not checked, you are prompted for a system administrator password in the next step of the installation workflow (see Section 3.10, “Authentication for the System Administrator “root””).This option automatically logs the current user in to the system when it starts. This is mainly useful if the computer is operated by only one user.
Warning: Automatic Login
With the automatic login enabled, the system boots straight into your desktop with no authentication. If you store sensitive data on your system, you should not enable this option if the computer can also be accessed by others.
In an environment where users are centrally managed (for example by NIS or LDAP) you may want to skip the creation of local users. Select in this case.
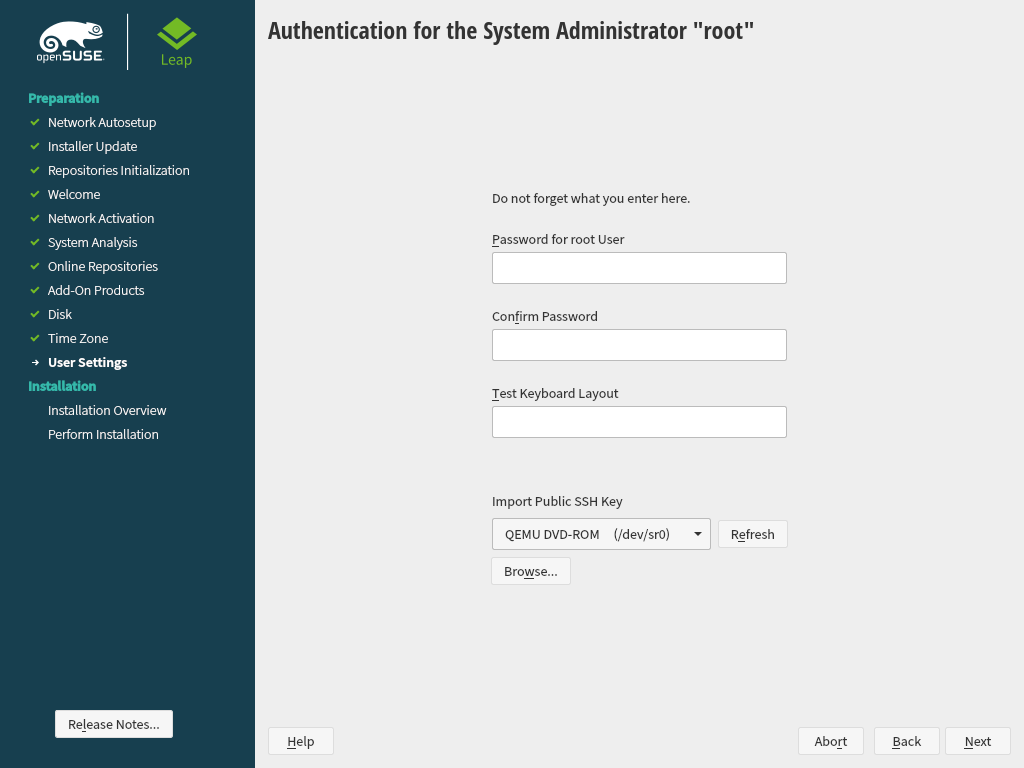
3.10 Authentication for the System Administrator “root” #Edit source
If you have not chosen in the previous step, you will be prompted to enter
a password for the System Administrator root or provide a public SSH
key. Otherwise this configuration step is skipped.
Figure 3.7: Authentication for the System Administrator root #
root is the name of the superuser, or the administrator of the system.
Unlike regular users, root has unlimited
rights to change the system configuration, install programs, and set up new
hardware. If users forget their passwords or have other problems with the
system, root can help. The root account should only be used for
system administration, maintenance, and repair. Logging in as root for
daily work is rather risky: a single mistake could lead to irretrievable
loss of system files.
For verification purposes, the password for root must be entered
twice. Do not forget the root password. After having been entered,
this password cannot be retrieved.
Tip: Passwords and Keyboard Layout
It is recommended to only use characters that are available on an English keyboard. In case of a system error or when you need to start your system in rescue mode a localized keyboard might not be available.
The root password can be changed any time later in the installed
system. To do so run YaST and start › .
Important: The root User
The user root has all the permissions needed to make changes to the
system. To carry out such tasks, the root password is required. You
cannot carry out any administrative tasks without this password.
In some situations it is preferred to access the system remotely via SSH using a public key. This screen allows you to select a public key from a medium.
The following procedure describes how to add a public SSH key from a USB stick. It works the same way with CD/DVD-ROM or from an existing partition. Proceed as follows:
Procedure 3.1: Adding a Public SSH Key for User root #
Insert into your computer the USB storage device containing the public SSH key. The public SSH key has the file extension
.pub.Click . You should see the device in the list selector under .
Click and select the public SSH key.
Proceed with .
In the summary, make sure to check under the SSH port. Click so it reads .
After the installation is finished, you can log in through SSH using the provided public SSH key.
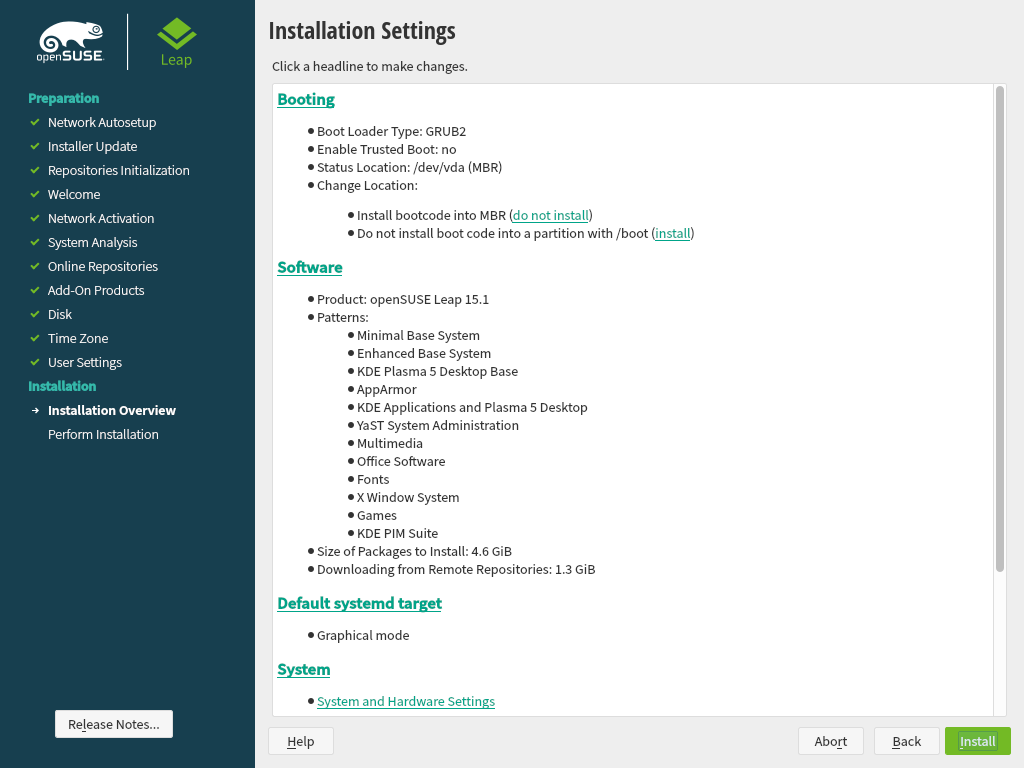
3.11 Installation Settings #Edit source
On the last step before the real installation takes place, you can alter installation settings suggested by the installer. To modify the suggestions, click the respective headline. After having made changes to a particular setting, you are always returned to the Installation Settings window, which is updated accordingly.
If you have added an SSH key for your root as mentioned in Procedure 3.1,
make sure to open the SSH port in the
settings.
Figure 3.8: Installation Settings #
3.11.1 #Edit source
openSUSE Leap contains several software patterns for various application purposes. The available choice of patterns and packages depends on your selection of modules and extensions.
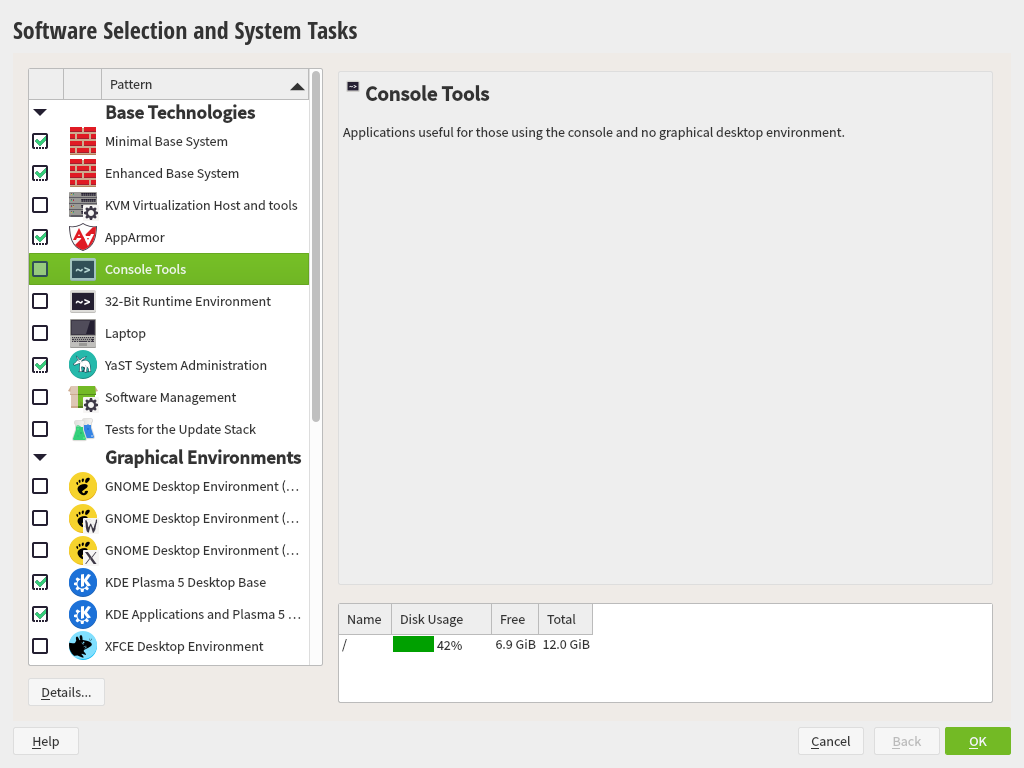
Click to open the screen where you can modify the pattern selection according to your needs. Select a pattern from the list and see a description in the right-hand part of the window.
Each pattern contains several software packages needed for specific functions (for example Multimedia or Office software). If you chose in the dialog choose a desktop environment from the list of available . For a more detailed selection based on software packages to install, select to switch to the YaST Software Manager.
Figure 3.9: Software Selection and System Tasks #
You can also install additional software packages or remove software packages from your system at any later time with the YaST Software Manager. For more information, refer to Chapter 10, Installing or Removing Software.
By default, openSUSE Leap uses the Wayland display server protocol.
Tip: Adding Secondary Languages
The language you selected with the first step of the installation will be used as the primary (default) language for the system. You can add secondary languages from within the dialog by choosing › › .
3.11.2 #Edit source
The installer proposes a boot configuration for your system. Other operating systems found on your computer, such as Microsoft Windows or other Linux installations, will automatically be detected and added to the boot loader. However, openSUSE Leap will be booted by default. Normally, you can leave these settings unchanged. If you need a custom setup, modify the proposal according to your needs. For information, see Book “Reference”, Chapter 12 “The Boot Loader GRUB 2”, Section 12.3 “Configuring the Boot Loader with YaST”.
Important: Software RAID 1
Booting a configuration where /boot resides on a
software RAID 1 device is supported, but it requires to install the boot
loader into the MBR ( › ). Having
/boot on software RAID devices with a level other
than RAID 1 is not supported.
3.11.3 #Edit source
The refer to kernel boot command line parameters for software mitigations that have been deployed to prevent CPU side-channel attacks. Click the highlighted entry to choose a different option. For details, see Book “Reference”, Chapter 12 “The Boot Loader GRUB 2” CPU Mitigations.
By default firewalld is enabled on all configured network interfaces.
To globally disable the firewall for this computer, click
(not recommended).
Note: Firewall Settings
If the firewall is activated, all interfaces are configured to be in the “External Zone”, where all ports are closed by default, ensuring maximum security. The only port you can open during the installation is port 22 (SSH), to allow remote access. All other services requiring network access (such as FTP, Samba, Web server, etc.) will only work after having adjusted the firewall settings. Refer to Book “Security Guide”, Chapter 17 “Masquerading and Firewalls” for more information.
To enable remote access via the secure shell (SSH), make sure the
SSH service is enabled and the SSH
port is open.
Tip: Existing SSH Host Keys
If you install openSUSE Leap on a machine with existing Linux installations, the installation routine imports an SSH host key. It chooses the host key with the most recent access time by default.
If you are performing a remote administration over VNC, you can also specify whether the machine should be accessible via VNC after the installation. Note that enabling VNC also requires you to set the to .
3.11.4 #Edit source
This category displays the current network settings (as automatically configured after booting into the installation, see Section 3.4) or as manually configured from the or dialog during the respective steps of the installation process. If you want to check or adjust the network settings at this stage (before performing the installation), click . This takes you to the YaST module. For details, see Book “Reference”, Chapter 13 “Basic Networking”, Section 13.4 “Configuring a Network Connection with YaST”.
3.11.5 #Edit source
openSUSE Leap can boot into two different targets (formerly known as “runlevels”). The target starts a display manager, whereas the target starts the command line interface.
The default target is . In case you have not installed the patterns, you need to change it to . If the system should be accessible via VNC, you need to choose .
3.11.6 #Edit source
If an existing Linux installation on your computer was detected, YaST
will import the most recent SSH host key found in
/etc/ssh by default, optionally including other files
in the directory as well. This makes it possible to reuse the SSH identity
of the existing installation, avoiding the REMOTE HOST
IDENTIFICATION HAS CHANGED warning on the first connection. Note
that this item is not shown in the installation summary if YaST has not
discovered any other installations. You have the following choices:
Select this option to import the SSH host key and optionally the configuration of an installed system. You can select the installation to import from in the option list below.
Enable this to copy other files in
/etc/sshto the installed system in addition to the host keys.
3.11.7 #Edit source
This screen lists all the hardware information the installer could obtain about your computer. When opened for the first time, the hardware detection is started. Depending on your system, this may take some time. Select any item in the list and click to see detailed information about the selected item. Use to save a detailed list to either the local file system or a removable device.
Advanced users can also change the and kernel settings by choosing . A screen with two tabs opens:
Each kernel driver contains a list of device IDs of all devices it supports. If a new device is not in any driver's database, the device is treated as unsupported, even if it can be used with an existing driver. You can add PCI IDs to a device driver here. Only advanced users should attempt to do so.
To add an ID, click and select whether to enter the data, or whether to choose from a list. Enter the required data. The is the directory name from
/sys/bus/pci/drivers—if empty, the name is used as the directory name. Existing entries can be managed with and .Change the here. If is chosen, the default setting for the respective architecture will be used. This setting can also be changed at any time later from the installed system. Refer to Book “System Analysis and Tuning Guide”, Chapter 12 “Tuning I/O Performance” for details on I/O tuning.
Also activate the here. These keys will let you issue basic commands (such as rebooting the system or writing kernel dumps) in case the system crashes. Enabling these keys is recommended when doing kernel development. Refer to https://www.kernel.org/doc/html/latest/admin-guide/sysrq.html for details.
3.12 Performing the Installation #Edit source
After configuring all installation settings, click in the Installation Settings window to start the installation. Some software may require a license confirmation. If your software selection includes such software, license confirmation dialogs are displayed. Click to install the software package. When not agreeing to the license, click and the software package will not be installed. In the dialog that follows, confirm with again.
The installation usually takes between 15 and 30 minutes, depending on the system performance and the selected software scope. After having prepared the hard disk and having saved and restored the user settings, the software installation starts. Choose to switch to the installation log or to read important up-to-date information that was not available when the manuals were printed.
After the software installation has completed, the system reboots into the new installation where you can log in. To customize the system configuration or to install additional software packages, start YaST.