Security and Hardening Guide
- Preface
- 1 Security and confidentiality
- I Authentication
- II Local security
- 9 Physical security
- 10 Software management
- 11 File management
- 12 Encrypting partitions and files
- 13 Storage encryption for hosted applications with cryptctl
- 14 User management
- 15 Restricting
cronandat - 16 Spectre/Meltdown checker
- 17 Configuring security settings with YaST
- 18 The Polkit authentication framework
- 19 Access control lists in Linux
- 20 Intrusion detection with AIDE
- III Network security
- IV Confining privileges with AppArmor
- 27 Introducing AppArmor
- 28 Getting started
- 29 Immunizing programs
- 30 Profile components and syntax
- 31 AppArmor profile repositories
- 32 Building and managing profiles with YaST
- 33 Building profiles from the command line
- 34 Profiling your Web applications using ChangeHat
- 35 Confining users with
pam_apparmor - 36 Managing profiled applications
- 37 Support
- 38 AppArmor glossary
- V SELinux
- VI The Linux Audit Framework
- A GNU licenses
16 Spectre/Meltdown checker #Edit source
Abstract#
spectre-meltdown-checker is a shell script to test if
your system is vulnerable to the several speculative execution
vulnerabilities that are in nearly all CPUs manufactured in the
past 20 years. This is a hardware flaw that potentially allows an attacker
to read all data on the system. On cloud computing services, where multiple
virtual machines are on a single physical host, an attacker can gain access
to all virtual machines. Fixing these vulnerabilities requires redesigning
and replacing CPUs. Until this happens, there are several software patches
that mitigate these vulnerabilities. If you have kept your SUSE systems
updated, all these patches should already be installed.
spectre-meltdown-checker generates a detailed report. It
is impossible to guarantee that your system is secure, but it shows you
which mitigations are in place, and potential vulnerabilities.
16.1 Using spectre-meltdown-checker #Edit source
Install the script, and then run it as root without any options:
#zypper in spectre-meltdown-checker#spectre-meltdown-checker.sh
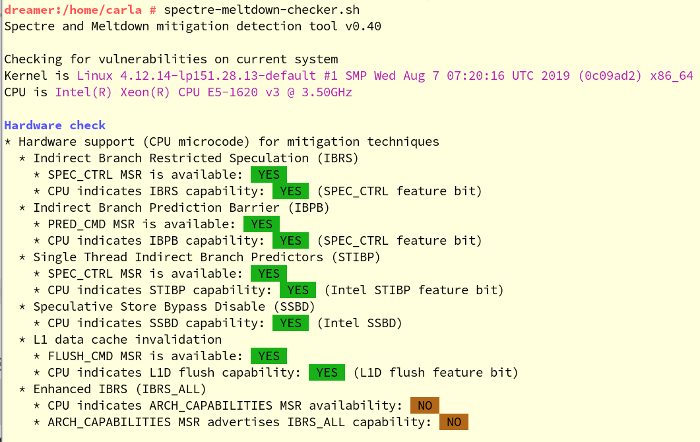
You see colorful output like Figure 16.1, “Output from spectre-meltdown-checker”:
Figure 16.1: Output from spectre-meltdown-checker #
spectre-meltdown-checker.sh --help lists all options. It
is useful to pipe plain text output, with no colors, to a file:
# spectre-meltdown-checker.sh --no-color| tee filename.txt
The previous examples are on a running system, which is the default. You may
also run spectre-meltdown-checker offline by specifying
the paths to the kernel, config and System.map files:
#cd /boot#spectre-meltdown-checker.sh \ --no-color \ --kernel vmlinuz-6.4.0-150600.9-default \ --config config-6.4.0-150600.9-default \ --map System.map-6.4.0-150600.9-default| tee filename.txt
Other useful options are:
- --verbose, -v
Increase verbosity; repeat for more verbosity, for example
-v -v -v- --explain
Print human-readable explanations
- --batch [short] [json] [nrpe] [prometheus]
Format output in various machine-readable formats
Important: --disclaimer option
spectre-meltdown-checker.sh --disclaimer provides
important information about what the script does, and does not do.
16.2 More information #Edit source
For more information, see the following references:
SUSE Knowledge Base article #7022937, Security Vulnerability: Spectre Variant 4 (Speculative Store Bypass) aka CVE-2018-3639: https://www.suse.com/support/kb/doc/?id=7022937
speed47/spectre-meltdown-checker source code on GitHub, with detailed references to relevant Common Vulnerabilities and Exposures (CVE): https://github.com/speed47/spectre-meltdown-checker
SUSE Blog article, Meltdown and Spectre Performance: https://www.suse.com/c/meltdown-spectre-performance/
SUSE Knowledge Base article #7022512, providing information on architectures, CVEs, and mitigations: https://www.suse.com/support/kb/doc/?id=7022512